OWASP Top 10: Injection - What it is and How to Protect Our Applications OWASP Top 10: Injection - What it is and How to Protect Our Applications OWASP Top 10: Injection -

OWASP Top 10: #1 Injection and #2 Broken Authentication – Knowlton Center for Career Exploration | Denison University

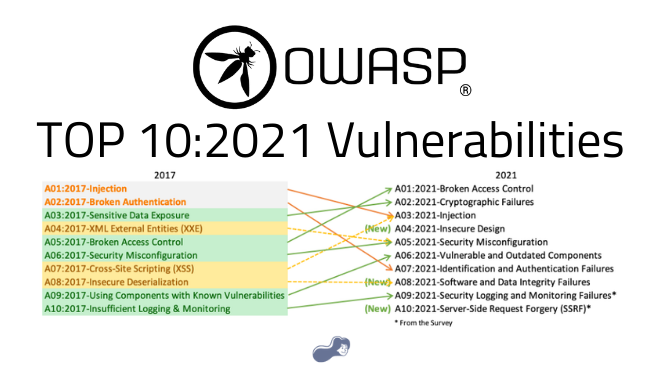
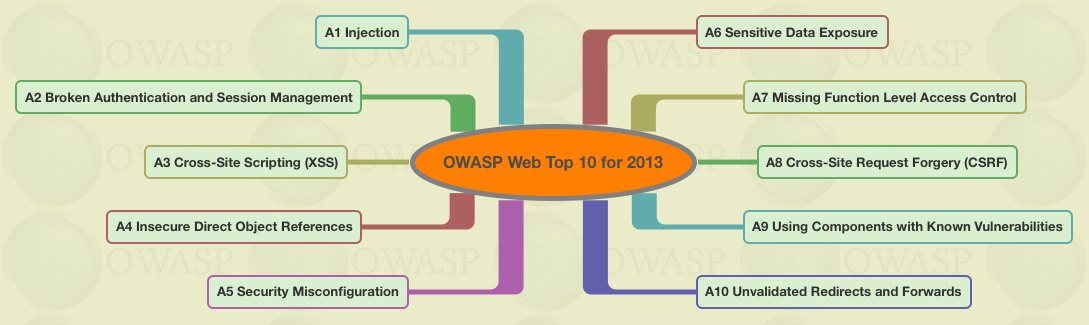
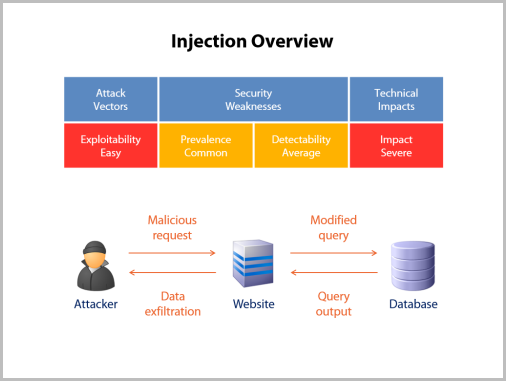
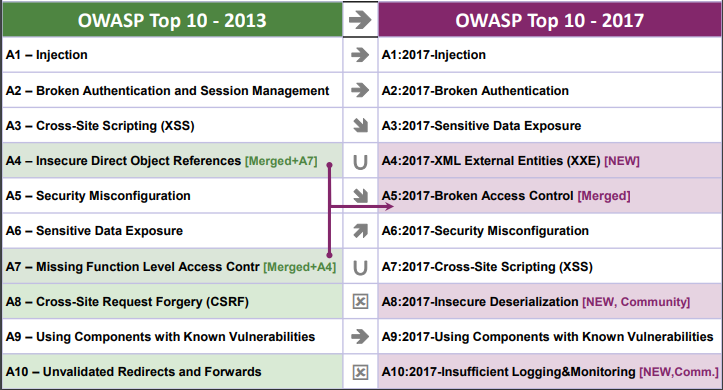
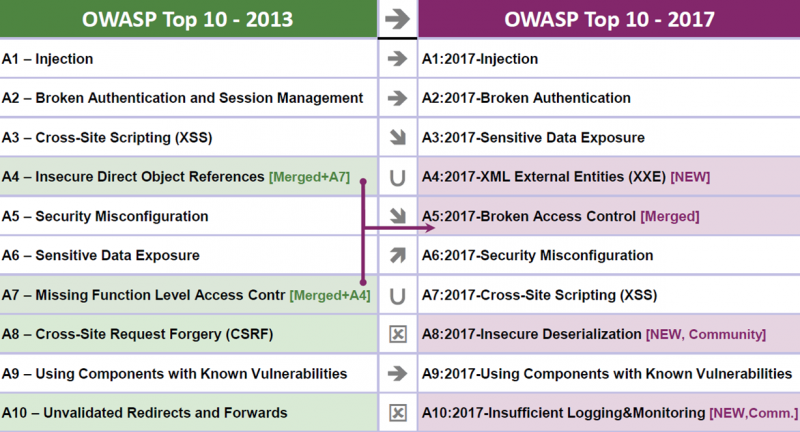
Try Hack Me - 🔝10 OWASP stands for the Open Web Application Security Project, an online community that produces articles, methodologies, documentation, tools, and technologies in the field of web application security.